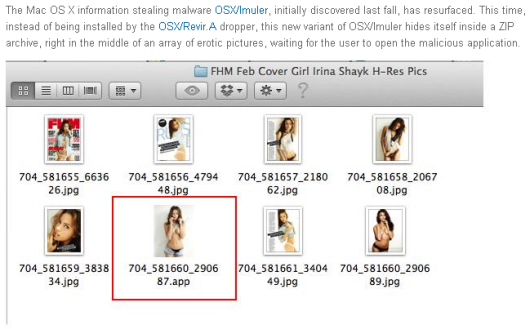
[Security] Malware OSX/Imuler OSX/Revir.A dropper
This new variant is very similar to its ancestors in terms of command-and-control (C&C ) communication and functionalities. (OSX/Imuler is an information stealer that can gather and transmit files, screenshots, and other data to a remote server.) The network protocol is still HTTP-based and the payload is compressed with zlib. The hardcoded C&C domain now being used is a new one, registered on February 13th, 2012 via a Chinese registrar. The domain points to the same IP address as the previous variants, located in the USA and still active at time of writing.
This all seems to indicate that the new variant was most likely released to improve its anti-virus evasion.
OSX/Imuler has the functionality to upload arbitrary local files to the C&C. A specialized separate executable named CurlUpload, downloaded from the C&C every time the malware starts, is used to perform the operation. This stand-alone executable, first seen in early 2011, presents interesting strings that suggest it was initially built for Win32 but later recompiled for OS X:
ESET security software (including ESET Cybersecurity for Mac) since signature update 6970 detects this new variant as OSX/Imuler.C.
MD5 of the files analyzed:
7dba3a178662e7ff904d12f260f0fff3 (Installer)
9d2462920fdaed5e360875fb0cf8274f (malicious payload))
e00a280ad29440dcaab42ad093bcaafd (uploader module)
Big thanks to my colleague Marc-Étienne M. Léveillé for his work on this investigation.
[ Via Blog Eset ]


Comments
Post a Comment
Để lại góp ý của bạn để blog của mình hoàn thiện hơn :))