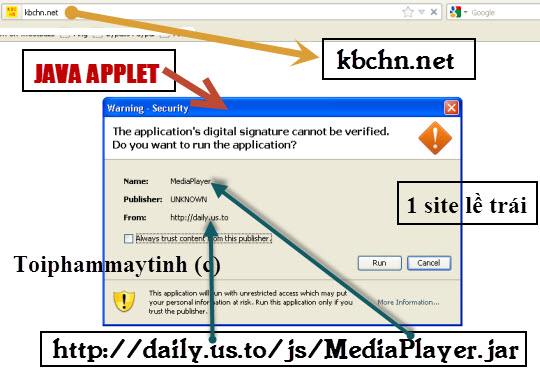
Introduction TimThumb is definitely one of the most valuable files (i.e., PHP scripts), that I want to find during a Penetration Test, as earlier versions between 1.0 and 1.32 has a flaw that enables an attacker to remotely cache PHP scripts[1,2], allowing remote code execution. It is an image tool often used in WordPress themes, making cropping, zooming and resizing a lot easier, and it is open source of course. The amount of websites that use this script are extreme, but most have hopefully upgraded to the newest, completely re-written version 2.X, that combats the critical remote cache vulnerability but also other problems too. At least 328 themes and 76 plug-ins [4], use this script where the file is occasionally renamed, meaning an empty search result for “timthumb.php”, is not equal to it isn’t there. One of the ways to search for this script, is to use WPScan [5], another is to use shell scripting as shown in a later figure. WPScan is a...