[Security] Overdrive Spam Campaign Targets Business Banks by by Andrew Brandt
A small trickle of badly-malformed spam email turned into a flood last week as hundreds of copycat messages per minute flooded inboxes we use to collect samples. The malware delivered by the spammed links isn’t your garden variety bank phishing Trojan. This one has its eyes on a specific prize: It wants the credentials for online banks that cater specifically to business users — both the employees’ passwords and those of the banks’ customers.
The campaign, covered in its early stages in the previous post, employs Google’s shortlinking service, goo.gl. The exploit, delivered at the other end of that shortlink, rapidly snares victims. In several test runs, the victim computer was infected in well under 30 seconds.
The first malware payload appears to function as a traffic controller of sorts, helping guide additional payloads to the victim PC. It does this work at the behest of a botmaster using95.57.120.104, an IP address that geolocation services place in Kazakhstan. The malware communicates with its command-and-control server using SSL encryption, but we have a secret weapon: We can decrypt your CnC traffic, and we see what you did here.
The spam messages delivering the link are horribly malformed. The From: address in the message is a random-looking group of numbers, followed by names that sound like some sort of business department, with occasional random characters strewn throughout. A lot of them look likeNetwork_RulesDepartment or Business_Account Departmentu. Sounds legit.
The subject line references several banks and investment service companies with a focus on commercial customers, including BPD Bank Online, Webster Bank, Bank of the West, NetTeller (a UK-based payment service similar to PayPal), and First Data’s FundsXpress, and contained the usual (fragmentary) social engineering hook: Phrases like ACH Transfer Rejected, Transfer was disallowed, and Account frozen occur with regularity; There are too many examples to list them all here.
But what happened after the infection took place was the most interesting part. AV companies call the initial infectious code SmokeLoader, Cridex, Dofoil, or Qbot, depending on who you ask. Payloads, unfortunately, were detected by fewer antivirus engines (initially none), but the results Virustotal does return includes some of these same names.
Immediately, we began to see the initial malware executable beacon out to its command-and-control server. It used four different domains on a rotating schedule — the four URLs embedded in the executable, all of which resolve to one IP address. It makes this connection about once an hour, shrinkwrapped in a protective layer of SSL encryption, and performs a DNS lookup of one CnC domain every 20 minutes.
Normally, this traffic would be completely unreadable. The most you might see under normal circumstances is the SSL certificate from the host, which in this case came from the Kazakh server hosted by gohost.kz, a regional ISP.
But these were not normal circumstances. We cracked that SSL connection like an egg on the sidewalk, and this is what we put back together again:
Hey there, Humpty. This is the unencrypted pingback from Qbot. Smallest name wins. As you can see, it’s sending the name of the user account under which the Trojan is running (Hi!), as well as the name of the process it hooked (explorer.exe) on the infected box, and a timestamp (in UNIX epoch format).
We didn’t try to decode the string of hex circled in yellow; It looks a bit like what two other botnet Trojans — RBot and SDbot — use as a unique identifier for the infected machine, but to say that’s what’s happening here would be pure speculation. I am, however, the botnet owner’s F0E, so at least he/she/it got that part right.
Filtering out all other traffic, the heartbeat packets even look kind of like a heartbeat, as shown on an ECG.
Within seconds of the first infection, however, the bot was pulling down additional malware, which we could reconstruct from the packets. Note that this was also transmitted over SSL (port 443).
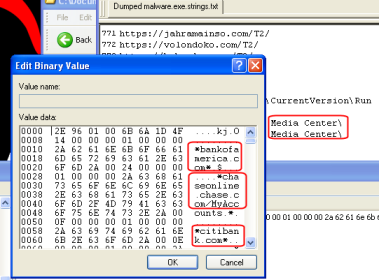
One of the payloads set itself up as a file named KB00124251.exe in the Application Data directory of the currently logged-in user’s profile, and sets a run key to start itself at reboot. It all sounds pretty rudimentary until you see the other registry key it sets: Under the HKEY_CURRENT_USER hive, it creates a new key in Software\Microsoft\Windows Media Center\ with a random, eight-hexadecimal-character name.
Inside that key, it creates one massive value. By comparison, the longest that most registry key values get are only a few tens of characters long. This one was 208,160 characters long. And you can bet there was some interesting stuff in there.
Inside that registry key, virtually in plain view, is a huge amount of text. For lack of a better name, I’m going to call the parts which determine the Web site the Trojan targets URI fragments. These strings, wrapped on either end in an asterisk, are made up of full domain names, or fragments of domain names, or fragments of domain names with specific paths, or just paths without domains. It seems to use the fragments in its triggering mechanism.
All told, a URI fragment tripwire has been placed in front of the domain names of roughly 300 banks, credit unions, and financial institutions, most based in the US. The paths listed in the tripwire code point unquestionably to the banks’ and credit unions’ business account holders — or in some cases, employees — as the primary target.
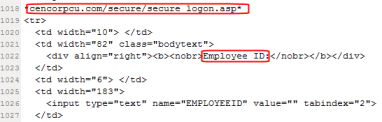
The bot process, hooked into explorer.exe and rootkitted, apparently can inject HTML into browser pages. To carefully control this process, the bot only performs the HTML injection when the right URI fragment appears in the browser’s Address Bar. The screen above demonstrates just how specific some of this injection can be; Employees of Central Corporate Credit Union in Southfield, Michigan: The Kazakh botmasters want your passwords, and they have figured out how to get them.
Some of the injections are very simple.
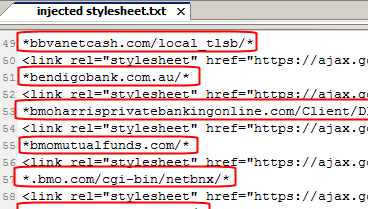
One of the things it tries to inject is a stylesheet fromhttps://ajax.googleapis.com/ajax/libs/jqueryui/1.8.11/themes/hot-sneaks/jquery-ui.css. It target 127 different banks with this specific injection. I’m not sure what hot sneaks it’s trying to pull with this one, but I’m sure they aren’t what the jquery team envisioned, and the study of just that piece of the attack deserves closer scrutiny. But, in the short term, whoever is in charge of that ajax server could render this element of the attack useless just by moving that css to a different directory path, permanently.
And some of the injections are really, really complex, like this one, which targets Sberbank, Russia’s largest bank:
Wow, is that a bit of commentary from the injection code author? Does the author think Sberbank’s protection is so fragile, so delicate, and that this injection scripting they built is so sophisticated, that they can shatter Sberbank’s protection like it was porcelain, so they named a variable they use to inject code after something breakable…fine bone china, anyone?
Well it might be, but even after creating all that weirdly obfuscated injected Javascript code, these MENSA candidates can’t double-check the spelling of the word. Nice one, morons.
If you’re feeling left out, social network users, don’t: The tripwire also lists the domains for Twitter, Facebook, Blogger, Flickr, and LiveJournal (really?) login pages, as well. I hear LJ is popular in Russia.
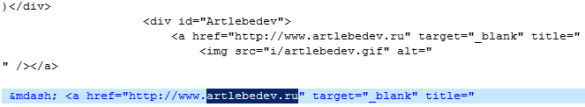
And the most bizarre twist: The injection code includes a reference to the Web site of the Russian industrial designer Artemy Lebedev, who operates a no bullshit design studio from Moscow, Kiev, and New York. Every hardcore geek I know drools over the company’s Optimus keyboards, but I don’t know any who would go to this length to get one. Funny thing, there is a connection between Art. Lebedev Studio and one target: The GIF icon that appears at the bottom of the login page for telebank.ru, one of the banking targets and, presumably, a Web design customer.
The thing I can’t get over with stuff like this, is the realization that someone — seemingly, a well-funded, dedicated, intelligent collective of sociopaths — spent an awful lot of time putting together specific lists of targeted login pages, and their unique characteristics, and built this thing with sophisticated knowledge of how to attack hundreds of different Web sites, solely for the purpose ofstealing. What a waste of human potential.
[ Via http://blog.soleranetworks.com ]
The campaign, covered in its early stages in the previous post, employs Google’s shortlinking service, goo.gl. The exploit, delivered at the other end of that shortlink, rapidly snares victims. In several test runs, the victim computer was infected in well under 30 seconds.
The first malware payload appears to function as a traffic controller of sorts, helping guide additional payloads to the victim PC. It does this work at the behest of a botmaster using95.57.120.104, an IP address that geolocation services place in Kazakhstan. The malware communicates with its command-and-control server using SSL encryption, but we have a secret weapon: We can decrypt your CnC traffic, and we see what you did here.
The spam messages delivering the link are horribly malformed. The From: address in the message is a random-looking group of numbers, followed by names that sound like some sort of business department, with occasional random characters strewn throughout. A lot of them look likeNetwork_RulesDepartment or Business_Account Departmentu. Sounds legit.
The subject line references several banks and investment service companies with a focus on commercial customers, including BPD Bank Online, Webster Bank, Bank of the West, NetTeller (a UK-based payment service similar to PayPal), and First Data’s FundsXpress, and contained the usual (fragmentary) social engineering hook: Phrases like ACH Transfer Rejected, Transfer was disallowed, and Account frozen occur with regularity; There are too many examples to list them all here.
But what happened after the infection took place was the most interesting part. AV companies call the initial infectious code SmokeLoader, Cridex, Dofoil, or Qbot, depending on who you ask. Payloads, unfortunately, were detected by fewer antivirus engines (initially none), but the results Virustotal does return includes some of these same names.
Immediately, we began to see the initial malware executable beacon out to its command-and-control server. It used four different domains on a rotating schedule — the four URLs embedded in the executable, all of which resolve to one IP address. It makes this connection about once an hour, shrinkwrapped in a protective layer of SSL encryption, and performs a DNS lookup of one CnC domain every 20 minutes.
Normally, this traffic would be completely unreadable. The most you might see under normal circumstances is the SSL certificate from the host, which in this case came from the Kazakh server hosted by gohost.kz, a regional ISP.
But these were not normal circumstances. We cracked that SSL connection like an egg on the sidewalk, and this is what we put back together again:
Hey there, Humpty. This is the unencrypted pingback from Qbot. Smallest name wins. As you can see, it’s sending the name of the user account under which the Trojan is running (Hi!), as well as the name of the process it hooked (explorer.exe) on the infected box, and a timestamp (in UNIX epoch format).
We didn’t try to decode the string of hex circled in yellow; It looks a bit like what two other botnet Trojans — RBot and SDbot — use as a unique identifier for the infected machine, but to say that’s what’s happening here would be pure speculation. I am, however, the botnet owner’s F0E, so at least he/she/it got that part right.
Filtering out all other traffic, the heartbeat packets even look kind of like a heartbeat, as shown on an ECG.
Within seconds of the first infection, however, the bot was pulling down additional malware, which we could reconstruct from the packets. Note that this was also transmitted over SSL (port 443).
One of the payloads set itself up as a file named KB00124251.exe in the Application Data directory of the currently logged-in user’s profile, and sets a run key to start itself at reboot. It all sounds pretty rudimentary until you see the other registry key it sets: Under the HKEY_CURRENT_USER hive, it creates a new key in Software\Microsoft\Windows Media Center\ with a random, eight-hexadecimal-character name.
Inside that key, it creates one massive value. By comparison, the longest that most registry key values get are only a few tens of characters long. This one was 208,160 characters long. And you can bet there was some interesting stuff in there.
Inside that registry key, virtually in plain view, is a huge amount of text. For lack of a better name, I’m going to call the parts which determine the Web site the Trojan targets URI fragments. These strings, wrapped on either end in an asterisk, are made up of full domain names, or fragments of domain names, or fragments of domain names with specific paths, or just paths without domains. It seems to use the fragments in its triggering mechanism.
All told, a URI fragment tripwire has been placed in front of the domain names of roughly 300 banks, credit unions, and financial institutions, most based in the US. The paths listed in the tripwire code point unquestionably to the banks’ and credit unions’ business account holders — or in some cases, employees — as the primary target.
The bot process, hooked into explorer.exe and rootkitted, apparently can inject HTML into browser pages. To carefully control this process, the bot only performs the HTML injection when the right URI fragment appears in the browser’s Address Bar. The screen above demonstrates just how specific some of this injection can be; Employees of Central Corporate Credit Union in Southfield, Michigan: The Kazakh botmasters want your passwords, and they have figured out how to get them.
Some of the injections are very simple.
One of the things it tries to inject is a stylesheet fromhttps://ajax.googleapis.com/ajax/libs/jqueryui/1.8.11/themes/hot-sneaks/jquery-ui.css. It target 127 different banks with this specific injection. I’m not sure what hot sneaks it’s trying to pull with this one, but I’m sure they aren’t what the jquery team envisioned, and the study of just that piece of the attack deserves closer scrutiny. But, in the short term, whoever is in charge of that ajax server could render this element of the attack useless just by moving that css to a different directory path, permanently.
And some of the injections are really, really complex, like this one, which targets Sberbank, Russia’s largest bank:
Wow, is that a bit of commentary from the injection code author? Does the author think Sberbank’s protection is so fragile, so delicate, and that this injection scripting they built is so sophisticated, that they can shatter Sberbank’s protection like it was porcelain, so they named a variable they use to inject code after something breakable…fine bone china, anyone?
Well it might be, but even after creating all that weirdly obfuscated injected Javascript code, these MENSA candidates can’t double-check the spelling of the word. Nice one, morons.
If you’re feeling left out, social network users, don’t: The tripwire also lists the domains for Twitter, Facebook, Blogger, Flickr, and LiveJournal (really?) login pages, as well. I hear LJ is popular in Russia.
And the most bizarre twist: The injection code includes a reference to the Web site of the Russian industrial designer Artemy Lebedev, who operates a no bullshit design studio from Moscow, Kiev, and New York. Every hardcore geek I know drools over the company’s Optimus keyboards, but I don’t know any who would go to this length to get one. Funny thing, there is a connection between Art. Lebedev Studio and one target: The GIF icon that appears at the bottom of the login page for telebank.ru, one of the banking targets and, presumably, a Web design customer.
The thing I can’t get over with stuff like this, is the realization that someone — seemingly, a well-funded, dedicated, intelligent collective of sociopaths — spent an awful lot of time putting together specific lists of targeted login pages, and their unique characteristics, and built this thing with sophisticated knowledge of how to attack hundreds of different Web sites, solely for the purpose ofstealing. What a waste of human potential.
[ Via http://blog.soleranetworks.com ]









Comments
Post a Comment
Để lại góp ý của bạn để blog của mình hoàn thiện hơn :))