[Security] Malware exploits death of North Korea's Kim Jong il
As expected, malware developers and scam artists have greeted the death of North Korea's dictatorial leader, Kim Jong-il, with Black Hat SEO and Social Engineering attacks. The Supreme Leader of the Democratic People's Republic of Korea suffered a heart attack on a train journey last month and a steady stream of schemes to exploit the news has been observed around the world. ESET Laboratories in Latin America found malware being spread through a fake YouTube video:

These videos were spotted in the days immediately after Kim Jong-il's death and preyed on people's natural curiosity. As you can see, the user is encouraged to click on a link to see the full story. By accessing the link, a new page is opened that appears to offer unlimited TV shows and movies. It also requests the installation of a toolbar to the browser:

When the user starts the installation, an application is automatically copied to the computer before the browser download manager sees a new incoming file. This type of file usually contains, in addition to advertising tools, other types of threats such as spyware or bots. These threats typically gain entry to end-user systems through tempting offers that encourage users to download applications. In this case, the incentive is an offer of free access to popular television series and movies over the Internet.
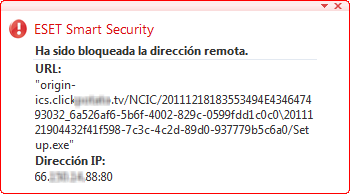 Note: ESET users are protected against this particular threat because the infections web sites are detected by our anti-malware products. Here you can see the alert shown to users of the Spanish language version of ESET Smart Security.
Note: ESET users are protected against this particular threat because the infections web sites are detected by our anti-malware products. Here you can see the alert shown to users of the Spanish language version of ESET Smart Security.Numerous other attempts to use the news of Kim Jong-il's demise have been observed. For example, our colleagues in India report a warning from the Indian Computer Emergency Response Team (CERT-In) regarding a spam campaign in that country which is distributing malware in a file called: "brief_introduction_of_kim_jong_Ill_pdf.pdf". The file exploits vulnerabilities in Adobe Reader and Acrobat to enable remote code execution in the victim system. Users are advised to make sure they have the latest Adobe Reader and Flash patches installed.
However, even when you are using up-to-date software and running strong anti-malware, you should still avoid clicking on links of dubious origin. Breaking news stories are best viewed directly from trusted sites or known media resources to minimize the chance of infecting the system.
Via http://blog.eset.com




Comments
Post a Comment
Để lại góp ý của bạn để blog của mình hoàn thiện hơn :))