[Security] Facebook Fakebook: New Trends in Carberp Activity by David Harley
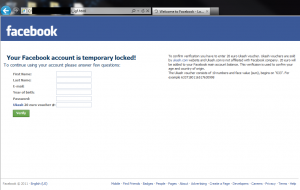
This month we discovered some new facts relating to Win32/Carberp trojan activity. We have spent a lot of time writing about Carberp already, but interesting information is still coming to light. The first interesting information to attract our attention recently concerned stealing money from Facebook users. Before then we hadn’t seen Carberp activity targeting social network users. The scheme used here for financial fraud is simple: if the victim attempts to log in to Facebook, he sees instead a fake Facebook page displaying the message “Your Facebook account is temporary locked!”
Figure 1: Fake Facebook Lockout
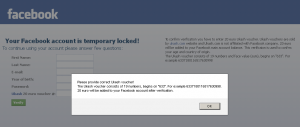
The fine print tells the victim to enter details of a "20 euro Ukash voucher" which can be purchased at ukash.com, assuring the victim that "20 euro will be added to your Facebook main account balance." If the victim enters information considered to be invalid – i.e. doesn’t take the hint and supply details for a 20 Euro Ukash voucher to “confirm verification” – then the following warning message is displayed, insisting that a valid Ukash voucher number be entered:
Figure 2: Demanding e-Cash
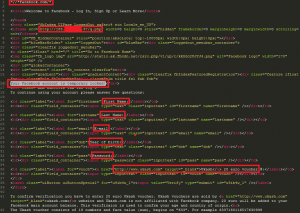
This sample of Carberp doesn’t include bootkit code, but in user-mode the injected module looks the same as the latest sample that does include the bootkit (http://blog.eset.com/2011/12/04/carberp-blackhole-growing-fraud-incidents). The most interesting detail of this behavior is that this is not a new version/modification of the Carberp trojan, but simply a special configuration file that contains the full html code for the fake Facebook page. The decrypted configuration file contains only one web-injection rule for Facebook: *//*facebook.com/*
Figure 3: Faking Facebook
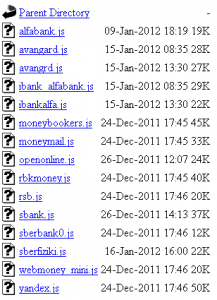
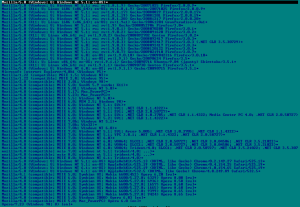
According to our data Carberp’s main activity is confined to the region of Russia and the former Soviet republics, and this activity centered on fraud targeting the major Russian banks and stealing money from RBS (Remote Banking Service) systems. Figure 4 shows the directory loaded with fresh files to introduce web-injects into online banking systems from the C&C panel:
Figure 4: Web-Injects
Up to now we hadn’t seen Carberp activity targeting the users of social networks, but it’s not so hard to add this functionality by introducing changes into the updated configuration file. Carberp intercepts many system functions and fraud functionality depend only on the rules for web-injects run from the configuration file or from special plugins. The Russian Federation is not the only country where this malware family is active. At this moment we know the facts of fraud related to the following banks based in non-Russian regions: Bank of America, CityBank, HSBC, CHASE, Nordea. But as before, the Russian Federation is the main region targeted by the Carberp attacks.
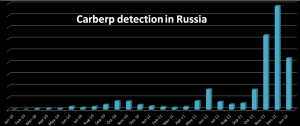
In early December, we noted an increase in the number of detections in the territory of Russia and the former Soviet republics (http://blog.eset.com/2011/11/21/evolution-of-win32carberp-going-deeper). But this trend can be seen in the statistics for December 2011 and late January 2012:
Figure 5: Carberp Detection in Russia
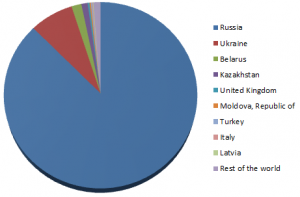
The Russian Federation is the country where the largest number of installations of Carberp has been seen, as confirmed by the statistics below:
Figure 6: Global Infection Statistics
Another interesting fact concerns a new DDoS plugin (Win32/Mishigy.AB) for Carberp. This DDoS plugin was developed in Delphi 7 and based on the network components from the Synapse TCP/IP library. Synapse components are very popular among cybercriminals for the creation of DDoS bots. A memorable example of a popular DDoS bot family based on this component is Win32/Delf.PYI (also known as a Dirt Jumper bot). The DDoS module provides the following types of attacks:
HTTP/HTTPS attacks
GET/POST attacks
download flood attacks
In order to bypass DDoS prevention systems multiple types of user-agents and legitimate web resources are used in the referrer string.
Figure 7: Bypassing DDoS Prevention Systems
Carberp is one of the biggest botnets in Russian Federation and total number of active bots is estimated to number millions of infected hosts. In the hands of the Carberp cybercrime group the DDoS module will be an effective means of attacking cybercrime groups, competing for the profits from malicious exploitation of online banking.
Our research continues …
Aleksandr Matrosov
David Harley
[Via]



Comments
Post a Comment
Để lại góp ý của bạn để blog của mình hoàn thiện hơn :))